CyberSecurity Solutions

CyberSecurity Management
Overview
At Ybrant Solutions, we understand that robust security is fundamental to the success of any digital transformation initiative. Our CyberSecurity solutions are designed to protect your critical assets, ensure compliance with regulations, and provide peace of mind as you navigate the complexities of the digital landscape.
What is CyberSecurity?
CyberSecurity refers to the protection of information systems against unauthorised access, use, disclosure, disruption, modification, or destruction. It encompasses a wide range of practices and technologies designed to safeguard data integrity, confidentiality, and availability.
Why We Need CyberSecurity:
- Data Protection: To protect sensitive and proprietary information from breaches and cyberattacks.
- Regulatory Compliance: To adhere to industry regulations and avoid legal penalties.
- Business Continuity: To ensure that business operations can continue without disruption in the event of a security incident.
- Reputation Management: To maintain the trust of customers, partners, and stakeholders by safeguarding their information.
Secure your critical assets today!
Our CyberSecurity Solution Areas
Authorisation, Authentication, Access Management

- Authorisation, Authentication, and Access Management are critical components of our security solutions:
- Authentication: Verifying the identity of users before granting access to resources. We implement robust authentication mechanisms such as multi-factor authentication (MFA) to enhance security.
- Authorisation: Determining what resources a user is permitted to access once authenticated. We use fine-grained authorisation policies to ensure users have the appropriate level of access.
- Access Management: Managing and enforcing access policies across the organization to ensure secure access to applications, systems, and data.
Identity & Access Management (IAM)

- Identity & Access Management involves ensuring that the right individuals have access to the right resources at the right times for the right reasons. Our IAM solutions include:
- User Provisioning and Deprovisioning: Automating the process of creating, managing, and removing user accounts across multiple systems and applications.
- Single Sign-On (SSO): Enabling users to log in once and gain access to multiple systems without being prompted to log in again.
- Role-Based Access Control (RBAC): Assigning access rights based on user roles within the organization to simplify access management and enhance security.
Identity Governance

- Identity Governance ensures that your organization can effectively manage and control access to critical systems and data. Our identity governance solutions include:
- Access Reviews: Regularly reviewing user access rights to ensure they are appropriate and compliant with policies.
- Compliance Reporting: Generating reports to demonstrate compliance with regulatory requirements and internal policies.
- Policy Enforcement: Implementing and enforcing security policies to prevent unauthorized access and ensure that user access aligns with business needs.
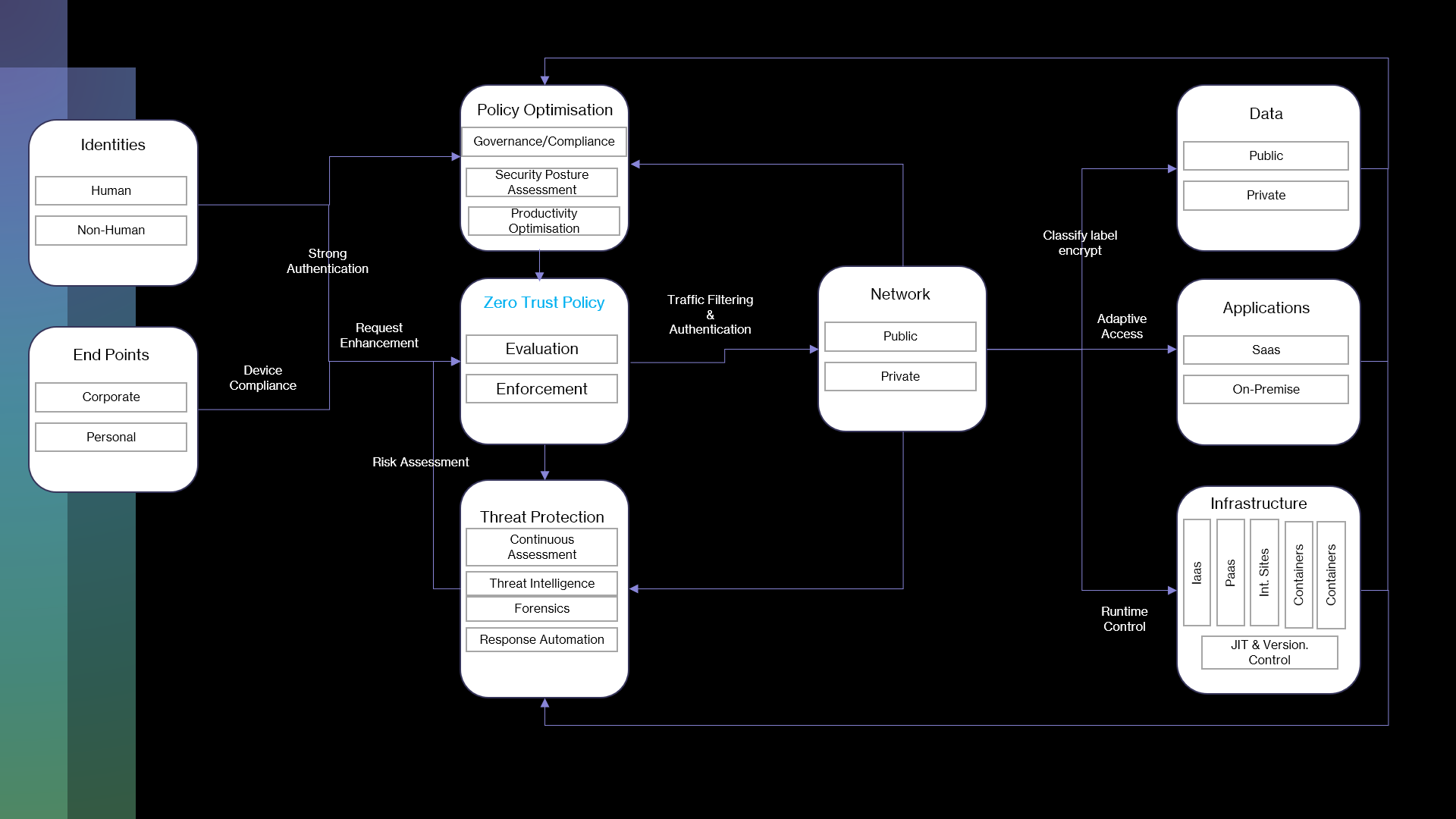
Zero Trust

At Ybrant Solutions our Zero Trust approach is based on a set of principles and pillars. Each organization must have a Zero Trust policy in place. It is a journey that each organization needs to embark on to secure their assets.
Safeguard! Don’t give away keys to your business. Work with Zero Trust
CyberSecurity Use Cases & Benefits
Use cases for Identity and Access Management
| Use Case | Detail | Benefit |
|---|---|---|
| 1. Financial Services Company (1,000-5,000 employees): Strengthening Security Posture | Enhancing IAM for Regulatory Compliance A mid-sized financial services firm is focused on bolstering its security posture to meet stringent regulatory requirements and protect sensitive customer data. They are implementing a robust IAM solution to ensure that only authorized personnel have access to critical systems and data. | Improved Security: The IAM solution ensures secure access to financial systems, reducing the risk of unauthorized access and data breaches. Regulatory Compliance: The system helps the company comply with financial regulations like GDPR and PCI-DSS by enforcing strong access controls and audit trails. Operational Efficiency: Automated access management reduces the administrative burden on IT teams and ensures timely updates to user access as roles change. |
| Healthcare Provider (5,000-15,000 employees): Migrating IAM to the Cloud | Cloud-Based IAM for Enhanced Accessibility and Security A large healthcare provider is migrating its IAM system to the cloud to enhance accessibility for staff and improve security measures. The shift to cloud-based IAM is part of the provider’s broader digital transformation strategy, aiming to secure patient data while enabling seamless access for healthcare professionals across multiple locations. | Cost Savings: Reduced IT infrastructure costs and maintenance efforts by migrating IAM to the cloud. Global Accessibility: Healthcare professionals can securely access the system from any location, ensuring continuity of care. Enhanced Security: The cloud IAM system includes advanced security features such as multi-factor authentication and real-time threat detection, protecting patient data from cyber threats. |
| Retail Enterprise (20,000-50,000 employees): Merging IAM Systems Post-Merger | Consolidating IAM for a Unified Security Framework Following a major merger, a large retail enterprise needs to consolidate IAM systems from both companies into a unified, integrated solution. The goal is to create a cohesive security framework that supports the organization’s expansive workforce and diverse retail operations. | Operational Efficiency: The unified IAM system streamlines user access management across the merged entities, reducing redundancy and improving user experience. Enhanced Security: Consolidation eliminates security gaps that may have existed between disparate IAM systems, ensuring consistent access controls. Cost Reduction: Merging IAM systems reduces licensing costs and lowers the complexity of managing multiple systems, freeing up resources for other strategic initiatives. |
Use cases for Identity and Access Governance
| Use Case | Detail | Benefit |
|---|---|---|
| Technology Company (1,000-5,000 employees): Enhancing Compliance and Auditability | Implementing IAG for Regulatory Compliance A mid-sized technology company that handles sensitive client data is focused on enhancing its compliance with industry regulations such as GDPR and SOC 2. They are implementing an Identity and Access Governance (IAG) solution to automate access certification processes, ensure role-based access controls (RBAC), and provide audit trails for all user activities. | Improved Compliance: Automates access reviews and certifications, ensuring that only authorized users have access to sensitive systems. Audit Readiness: Provides detailed audit trails and reports, making it easier to demonstrate compliance during regulatory audits. Risk Reduction: Reduces the risk of unauthorized access and data breaches by enforcing strict access governance policies. |
| Healthcare Institution (5,000-20,000 employees): Managing Complex User Roles and Access Rights | Role-Based IAG in a Complex Healthcare Environment A large healthcare institution with multiple departments and varying access needs is implementing an IAG solution to manage complex user roles and access rights. The goal is to ensure that healthcare professionals, administrators, and external contractors have the appropriate access to systems and data, while protecting patient privacy and meeting HIPAA requirements. | Streamlined Role Management: Simplifies the management of complex roles and access rights, ensuring that users have the right level of access based on their roles. Enhanced Security: Protects patient data by enforcing strict access controls and providing real-time monitoring of access activities. Operational Efficiency: Reduces the administrative burden of managing access rights across a large, diverse workforce. |
| Financial Institution (10,000-50,000 employees): Post-Merger Integration and Risk Management | IAG for Merging Entities in Financial Services Following a major merger, a large financial institution needs to integrate and harmonize the access governance policies of the merged entities. The goal is to create a unified Identity and Access Governance framework that supports the expanded organization while managing risks associated with access to financial systems and sensitive customer data. | Unified Governance Framework: Consolidates access governance policies across merged entities, ensuring consistency and reducing complexity. Risk Mitigation: Identifies and mitigates risks associated with excessive or inappropriate access, especially in a highly regulated financial environment. Improved Access Visibility: Provides centralized visibility into user access across the entire organization, enabling better decision-making and risk management. |
Zero Trust

Zero Trust Approach
It is imperative that organisations of any size must adopt Zero Trust Approach as part of their Security framework. Here are 5 reasons:
1)Improve user experience and productivity with Zero Trust
: : A Zero Trust approach empowers people to work productively and securely when, where, and how they want.
2)Apply Zero Trust to entire digital estate
: :Implementing Zero Trust requires a comprehensive vision and plan, prioritizing milestones based on the most important assets first.
3)Integrate verification and controls across security pillars
: :Unifying strategy and security policy with Zero Trust breaks down siloed information technology (IT) teams to enable better visibility and protection across the IT stack.
4)Monitor your security posture with strong governance
: :Enforcing strong governance with a Zero Trust approach includes validating business assertions, assessing security posture, and understanding the impact of security culture.
5)Automate to simplify and strengthen your security posture.
: : A Zero Trust approach prioritizes routine task automation, reducing manual efforts so security teams can focus on critical threats.

Zero Trust Principles
- Verify explicitly
- Always make security decisions using all available data points, including identity, location, device health, resource, data classification, and anomalies.
- Use least privilege access
- Limit access with just-in-time and just-enough-access (JIT/JEA) and risk-based adaptive polices.
- Assume breach
- Minimize blast radius with micro-segmentation, end-to end encryption, continuous monitoring, and automated threat detection and response.
Zero Trust Pillars
- ERP Technology Selection for Mid-Market Organisations: A Strategic Approach
- Why ERP Applications are Important for Mid-Market Organisations?
- Fixing Enterprise Architecture: Building a Roadmap for the Future
- Optimising Your Business with Value Stream Mapping and Management
- Zero Trust : CyberSecurity model for your organisation
- 100-Day Plan for ERP Discovery: Setting the Stage for Success
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-1140748312927744"
crossorigin="anonymous"></script>




